August 12, 2021
GRF Cybersecurity Risk Assessment and Scorecard Blog Series
Web applications are a top target for attackers. Hackers are constantly searching the web to find common vulnerabilities that they can use to exploit your website and data. Not having the proper security controls in place can result in an attacker bypassing authorization controls to steal confidential information. To protect your organization, it is crucial to identify and mitigate these vulnerabilities.
In 2020, Verizon conducted a Data Breach Investigation Report, which found that over 80 percent of hacks came through web application vulnerabilities.
Common Risks and Vulnerabilities
Cross-Site Request Forgery – Cross-Site Request Forgery (CSRF) is an attack that forces an end user to execute unwanted actions on a web application in which they’re currently authenticated. With a little help of social engineering (such as sending a link via email or chat), an attacker may trick the users of a web application into executing actions of the attacker’s choosing. If the victim is a normal user, a successful CSRF attack can force the user to perform state changing requests like transferring funds, changing their email address, and so forth. If the victim is an administrative account, CSRF can compromise the entire web application.
Clear Text Transmission of Sensitive Information – Communication via the internet can be intercepted easily depending on what network or WiFi you are connected to, especially on public resources such as airports, coffee shops, hotels, etc. Anyone else connected to the same network as you can see or “sniff” your internet traffic. Clear text or HTTP traffic is not encrypted and can be viewed by others. Encrypted traffic (HTTPS) is much more difficult to decipher.
Missing Encryption of sensitive data before storage or transmission – Encryption of sensitive data is extremely important. Is important to know that, just like other technologies, encryption protocols become obsolete and new ones are developed to ensure data is secure. Old, outdated encryption methods give end users a false sense of security. The data is encrypted but it does not secure the data because there are proven methods to decrypt the data.
Mitigating the Risks
While cybersecurity is a holistic approach, there are areas within application security that can be bolstered minimize the opportunity for a breach. Our recommendations for remediation of common high-risk items include:
- Make sure to always use strong encryption on web applications that require authentication or host sensitive information.
- Avoid mixing HTTP and HTTPS content. HTTP is not secure and is vulnerable to attacks.
- Detect and block excessive login or submission attempts. These attempts could be bots that are configured to take down your system with excess requests. Consider putting in a captcha request, so the user must verify that they are not a robot before entering.
- Consider applying Security Headers to web applications. Security headers are a key piece in website security and protect against a lot of common attacks.
By implementing these approaches to risks, you can develop a better cyber posture. It is also important to talk with your IT or web provider to make sure they are regularly checking these items to make sure they are implemented.
How GRF Can Help
It is important to scan your web applications regularly, as they are a top target for attackers. As part of our cybersecurity audits we offer a Cybersecurity Risk Assessment and Scorecard that scans your externally facing assets to identify any potential vulnerabilities within the applications that you currently have. We measure application-level problems using MITRE’s Common Weakness Enumerations (CWE), testing elements such as the transmission of data, encryption of data, cookies, HTTP, and more. The resulting report will show any risks to your organization and provide remediation steps.
For more information on GRF’s Cybersecurity Risk Assessment and Scorecard, or about our cybersecurity capabilities, reach out to our IT & Risk Supervisor Darren Hulem, CISA, Security +, or Risk Analyst Tom Brown, CAPM, through our contact us page.
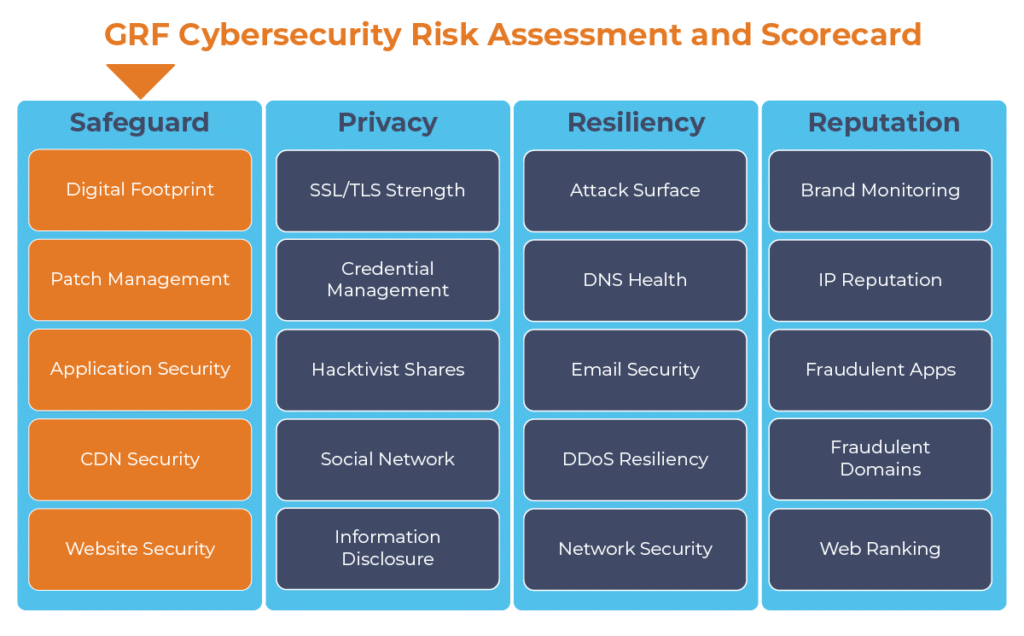
The digital transformation happening in the workplace requires heightened awareness of your organization’s cybersecurity posture. Managing the risks has become another full-time job. The GRF Cybersecurity Risk Assessment and Scorecard helps identify possible weaknesses and vulnerabilities by evaluating risk in 20 different categories. The scorecard will evaluate your cyber posture, propose remediation steps, and help eliminate vulnerabilities that your organization is facing.