August 12, 2021
GRF Cybersecurity Risk Assessment and Scorecard Blog Series
Identifying and mitigating website risks
Data breaches are costly, and the monetary risk is massive. According to a recent IBM report, the average total cost of a data breach in the U.S. is $8.64 million, but even a smaller number can be devastating, depending on the size of your organization. The risk to reputation and loss of trust from your users may be just as damaging and more difficult to restore.
Threat actors will often try to attack through the front door – the homepage of your website. They know they can cause reputation damage if they can access the webpage and deface it or inflict operational damage if they can disrupt your site’s functionality.
The nature of cyberattacks is always changing, requiring constant vigilance to monitor what vulnerabilities you have and address potential problems. Do you have the tools you need to secure your website from attacks?
What types of attacks are a threat?
The threat of being attacked by a cyber-criminal has been increasing every year. There are various ways that an attacker may utilize the weaknesses on your website to exploit both your organization and its users. Some common types of attacks include:
- Cross-Site Request Forgery – This happens when applications rely only on HTTP (unencrypted) cookies to identify a user request. This creates an opportunity for an attacker to utilize social engineering (like sending a link via chat) to a user. Clicking on the link enables the attacker to execute actions under the guise of that user – often without the user’s knowledge. This could allow the attacker to perform state-changing requests such as transferring funds or changing the user’s email address.
- SQL Injection – This allows for an attacker to run a SQL statement to inject code into your website without you knowing. This typically occurs within places that ask for user input like a user ID/ password field. Through the code they run, they may be able to access your database and gain the usernames/password of users in your organization.
- Brute Force Attack – Simply put, this is a trial and error method to guessing login information for a site. If your website does not have a limit on the number of times a user can enter credentials, then the attacker will be able to input as many username/password combinations as they want and try to gain access to your site.
What elements should you monitor?
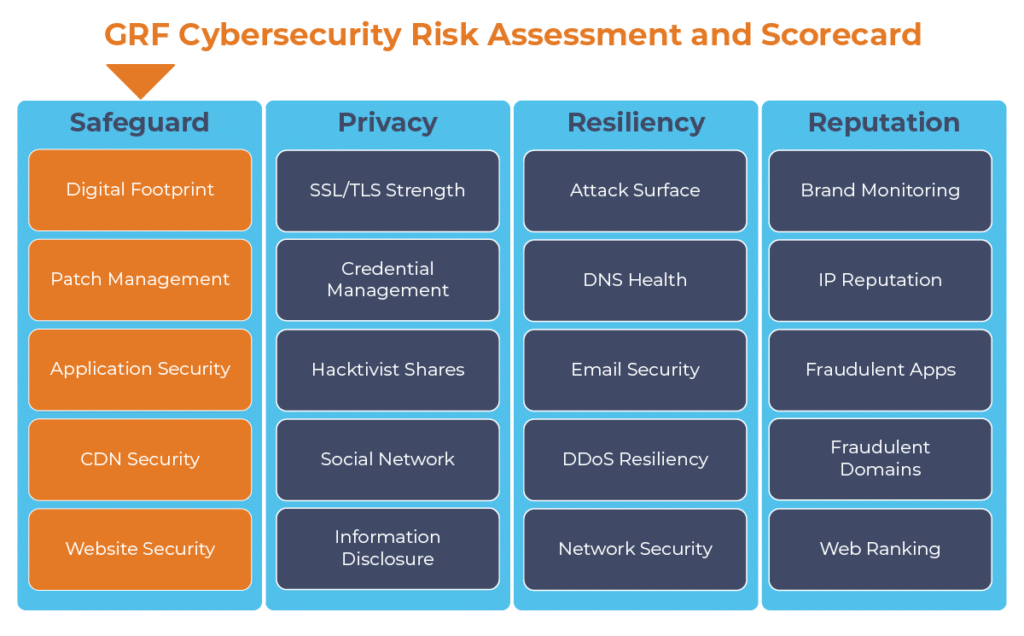
At GRF, we recommend you review several performance and security risk areas on your website:
SSL/TLS Strength – On your web browser, secured sites are indicated by a lock icon next to the web address. This indicates that the website is secure and is using encryption methods when exchanging and transporting data. User data needs to be protected to avoid attackers from stealing the contents being provided to the website. You should evaluate the SSL/TLS strength of your site against best practices to identify areas for improvement. Some common errors include missing an SSL certificate, not having the correct TLS version enabled, or using outdated cipher suites.
Performance – Users expect websites to deliver content quickly. Look at Google Page Speed Insights to determine how usable your website is from both the desktop and mobile versions. Within the results, there are recommendations for removing or adding certain items to improve your page performance.
Security Headers – Some common attacks including cross-site scripting, clickjacking, and code injection can be mitigated by including security headers within your website. By comparing against best practices, you will be able to see what headers you currently have and the ones that you are missing.
Patch Level – The main server that your website runs on may have vulnerabilities that could leave the website open to malicious attacks. Since Microsoft releases patches regularly, it is important to create a patch management policy to incorporate the new patches. Leaving your server vulnerable could spell trouble for your organization, as some of the biggest data breaches come from a lack of updates through patches.
Code Quality – Look for any mistakes within your HTML codes or redundant coding. Fixing these mistakes will improve the performance of your site.
How GRF can help
At GRF, we can review each of these categories to identify both risks and opportunities for your organization. We can provide you with recommendations to improve your cyber posture and improve end-user performance.
As part of our cybersecurity audits, our Cybersecurity Risk Assessment and Scorecard looks at 20 total categories that describe your organization’s cyber posture. Through our scan, we will assess your website security and identify potential vulnerabilities facing your organization. Our scan will provide a score (A, B, C, D, F) for each of the categories along with an overall score to help you understand your current security status and how you can improve. We will also provide remediation steps and ongoing support to help you improve your overall cyber landscape.
For more information on GRF’s Cybersecurity Risk Assessment and Scorecard, or about our cybersecurity capabilities, reach out to our IT & Risk Supervisor Darren Hulem, CISA, Security +, or Risk Analyst Tom Brown, CAPM, through our contact us page.
The digital transformation happening in the workplace requires heightened awareness of your organization’s cybersecurity posture. Managing the risks has become another full-time job. The GRF Cybersecurity Risk Assessment and Scorecard helps identify possible weaknesses and vulnerabilities by evaluating risk in 20 different categories. The scorecard will evaluate your cyber posture, propose remediation steps, and help eliminate vulnerabilities that your organization is facing.