October 4, 2021
GRF Cybersecurity Risk Assessment and Scorecard Blog Series
Simply put, Identity and Access Management (IAM) is the discipline of allowing the right individuals to have access to the right resources at the right times for the right reasons. As hackers have gotten more sophisticated, organizations must take steps to ensure that users attempting to gain access are authenticated (they are who they say they are), and that they have permission to access the data they are attempting to access.
Implementing security best practices and a credential management program is essential to prevent being a victim of an attack. Highly secure databases can still be beached if users’ access credentials are not properly secured. In fact, Ubiquiti – a major networking service provider – had a massive breach last year that exposed user credentials for millions of customers. Attackers were able to access Ubiquiti’s Amazon cloud servers by stealing an administrator’s credentials. Although Amazon secures their server hardware and software, the client is responsible for securing access, which Ubiquiti failed to do.
Privacy and security are two of the top risks facing organizations today, so it is important to understand how the authorization process works and how to manage it.
Access Management
At a high level, access issues fall into a large category. Access issues occur when users can access data that they shouldn’t be able to. Permission issues occur when a user has more permissions than they need to do their job, which can lead to an access violation. An access violation occurs when someone accesses or tries to access data that they are not authorized to see. To ensure users only have access to what they need to complete their job, it’s a good practice to utilize the method of least privilege. Controlling access within the system is the first step to maintaining a healthy IAM process and continues with identification and authorization.
User Identification
Most users are accustomed logging into a network or system by using a credentials such as a unique username and password, but as security has evolved, organizations are adopting more stringent requirements. Multi-factor authentication is a best practice in creating an effective credential management system and involves using two or more methods as a part of the authentication process.
Multi-factor authentication adds an extra step for a person to verify his or her identity. It may require providing something that you know (e.g. Password, PIN), something that you have (e.g. Smart Card, Common Access Card, or one-time password sent to phone), something that you are (e.g. Fingerprint, facial scan, eye scan), something you do (e.g. Handwriting, picture password), and/or where you are (e.g. Geolocation, inside a secure facility). At least two of these methods must be used to be considered multi-factor authentication. Utilizing MFA can help mitigate the risk of credential breaches that occur to maintain the integrity of your systems and only allow the correct users to log in to your network.
Credential Management
IAM allows for security and protection when accessing and utilizing your systems and network. However, there is a high risk of a data breach occurring due to compromised credentials. CyberNews reported that a database of over 3.2 billion unique pairs of clear text emails and passwords have been compiled and shared by hackers. It includes leaks from popular companies including Netflix, Gmail, and Yahoo. If any of your users utilized these websites and re-use their credentials, your company could be at risk of being attacked. An article from Security Magazine, states that 53% of people admit to using the same password across accounts which presents a major risk to your organization. Being aware of these leaked credentials is important to maintain an effective security posture.
IAM Security Best Practices
We recommend taking the steps below to make your systems more secure:
- Multi-Factor Authentication (MFA)
Passwords are not enough to keep your information safe. By implementing MFA, you add an extra layer of protection to your system, making it difficult for information to be stolen.
- Password Policy
Maintain a password policy that includes strong password requirements, changing of password at a set interval, and a top-down approach. If top management follows and enforces the policy, then everyone in the company can follow suit. Security needs to be an organizational mindset and not just an IT one.
- Password Manager
Ensure that employees are using password managers so that all of their passwords are different and strong. Many password managers are free and provide safety in case of a credential breach.
- Educate Your Employees
Organizations are constantly at risk of becoming a victim of a cyber-attack through phishing, malware, and lack of awareness. It is important to invest in cybersecurity training for all employees, having a cyber-policy, and making all employees aware of the process for reporting suspicious items/activity. No matter how strong your physical security is, all it takes is one click to allow an attacker into your network so investing in training and cyber awareness is essential.
- Encrypt Data
It is extremely important to protect all data by using encryption, so that if you are a victim of a breach, then your data will not be accessible to anyone who is not authorized to do so.
- Monitor Breached Credentials
There are over 5 billion breached emails and passwords available on the internet and underground forums. It is important to be aware when your organization’s credentials are breached so that passwords can be changed.
How GRF can help
Following these best practices is a great way to increase your organization’s cybersecurity posture. As part of our cybersecurity audits, we offer our Cybersecurity Risk Assessment and Scorecard to help take your organization’s cyber posture to the next level. We will provide an easy-to-read scorecard that identifies breached credentials and vulnerabilities, presents mitigation steps, and allows you to see where you can improve your security. Our team of risk professionals is here to provide support in your organization’s mission by protecting your assets.
For more information on GRF’s Cybersecurity Risk Assessment and Scorecard, or about our cybersecurity capabilities, reach out to our IT & Risk Supervisor Darren Hulem, CISA, Security +, or Risk Analyst Tom Brown, CAPM, through our contact us page.
For further Reading, refer to Identity and Access Management Benefits article from Identity-Theft-Awareness.com.
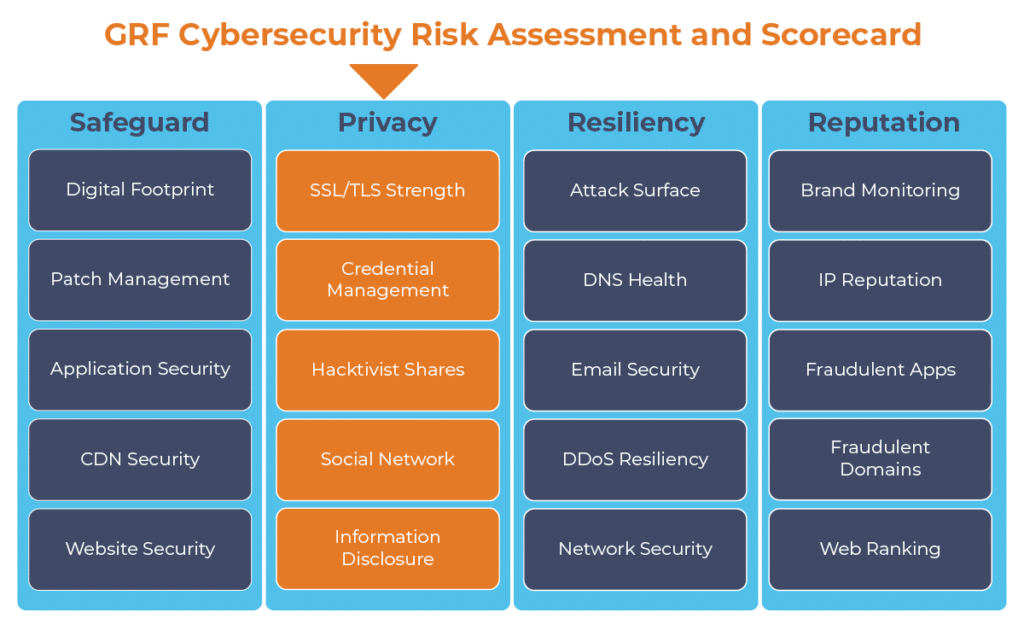
The digital transformation happening in the workplace requires heightened awareness of your organization’s cybersecurity posture. Managing the risks has become another full-time job. The GRF Cybersecurity Risk Assessment and Scorecard helps identify possible weaknesses and vulnerabilities by evaluating risk in 20 different categories. The scorecard will evaluate your cyber posture, propose remediation steps, and help eliminate vulnerabilities that your organization is facing.