Updated August 4, 2023
Nonprofits are more reliant on technology than ever before to deliver on their mission. The integration of digital technology into all aspects of the organization, or digital transformation, provides a number of new opportunities, but it also provides the possibility for additional security issues. Not only are there more ways to be attacked than ever before, cybersecurity breaches are constantly changing and hackers are becoming more sophisticated. Without proper cybersecurity, the organization’s critical activities are at risk the potential for reputational damage is real.
Digital transformation means that organizations must be proactive about their cybersecurity. Smaller organizations are particularly vulnerable due to budget constraints and staff resources, but they can benefit from adopting proven best practices from their larger counterparts.
Characteristics of Successful Cybersecurity Programs
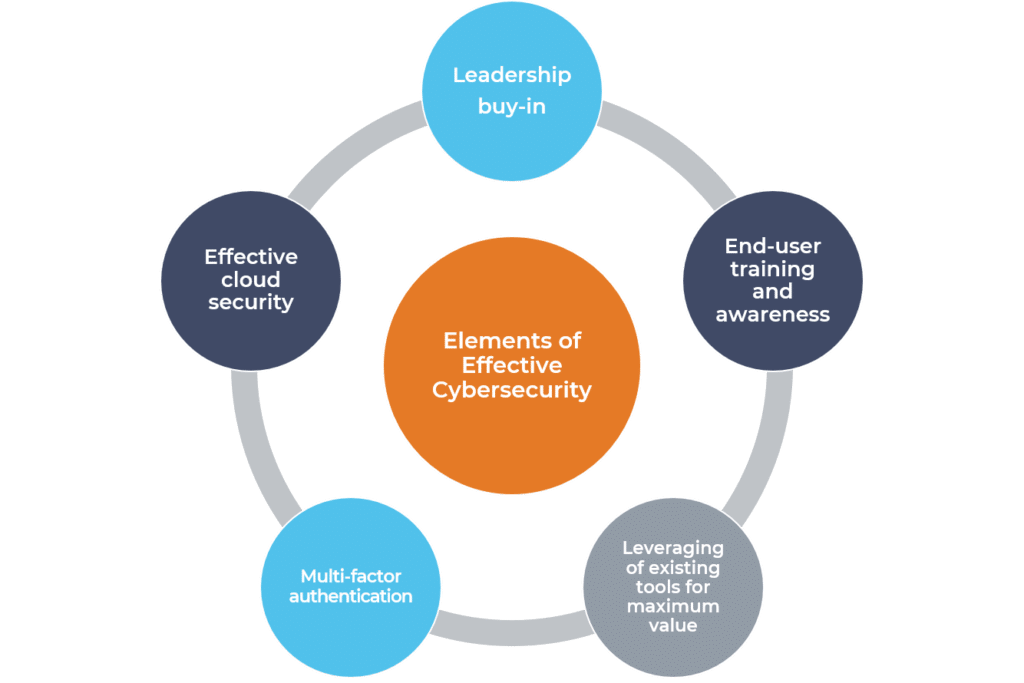
Successful cybersecurity programs include a combination of these elements.
Leadership Buy-In
Arguably, one of the most important aspects of cybersecurity for a nonprofit organization is leadership buy-in and support. While effective cybersecurity to protect the organization may seem like an obvious priority, in many cases there are detrimental enforcement issues. The cybersecurity “shield” may be in-place, but exceptions are made for specific users creating a weakness in the organization’s security posture. Common examples of these exceptions include exemption from the password policy, exclusion from multi-factor authentication or failure to complete cybersecurity training. Leadership support allows the organization’s information technology (IT) team to enable the appropriate cybersecurity measures and enforce critical policies and procedures.
End-user Training and Awareness
Equally important as leadership buy-in, end-user training and awareness is essential to the success of every cybersecurity program. While many organizations have employed spam filters, the best technology products still cannot stop every phishing attack. According to Verizon’s 2019 Data Breach Investigation’s Report, 94% of malware was delivered via email. Additionally, Symantec’s 2019 Internet Security Threat Report stated that, “65% of groups used spear-phishing as the primary infection vector.” With email being the main form of communication, it is critical to have continuous education for end-users. With an effective cybersecurity training and awareness program, all users are held to the same standard. This includes everyone from the C-suite and the IT department to anyone accessing the organization’s network resources.
Leveraging of existing tools for maximum value
When organizations get serious about cybersecurity, the conversation typically starts with a well-publicized breach and/or introduction to an advertised product or service. Contrary to popular belief, you do not need to spend a lot of money to protect your organization. Start with reviewing the products and services already in use, and evaluate whether these existing solutions are being deployed to their full potential. For example, does your organization require password complexity? Does it require passwords change after a certain period of time? Is there a policy that will lock the account after a pre-set number of failed login attempts? Many existing security features are disabled for convenience but they can leave a large gap in your organization’s cybersecurity posture.
Implementation of multi-factor authentication
One of the best values among the services available for cybersecurity is multi-factor authentication. Multi-factor authentication requires a second confirmation of the identity of the person accessing the system. For it to protect the organization though, all entry points into the network must require this additional form of authentication. If your organization currently uses Microsoft Office 365, multi-factor authentication is included in your license. Otherwise, there are multi-factor solutions for purchase including Duo, RSA and Yubikey. A little research will go a long way to ensure your peace of mind that the organization’s network has protection.
Effective cloud security
You have moved everything to the cloud so your cloud provider now handles your organization’s cybersecurity. Not so fast! Even though Amazon Web Services, Azure or Google Cloud is supplying infrastructure as a service, your organization is still responsible for configuration and proper set-up. They will not manage your operating system updates, nor will they lock down your network. In addition, if your configuration is incorrect, your data can be open to anyone online.
Cloud services are complex and very powerful, but misconfigurations can be catastrophic. By default, newly created S3 buckets in AWS block public access, but this was not always the case. According to security firm Skyhigh Networks, 7% of all S3 buckets (storage in AWS) have unrestricted public access and 35% are unencrypted. Some of these storage buckets have intended unrestricted access, but a large number of customers are unaware that they are not protected. In addition, just because public access is initially blocked by default does not stop someone from changing the access level later.
Resources
The elements described above should be part of your nonprofit’s arsenal to prevent a potential cybersecurity breach. While this list is not all-inclusive, it can be a starting point for any organization concerned about cybersecurity to consider. In addition to being best practices employed as part of sophisticated cybersecurity programs, many of these elements may already be present in your organization awaiting deployment. For more on this topic, including an overview of our cybersecurity scorecard, visit GRF’s Cybersecurity and Privacy Risk page.
For more resources regarding cybersecurity for nonprofits, including recent blog posts on the case for virtual chief information security officers and vulnerability scanning and penetration testing, visit our Resources page. If you have questions regarding your organization’s security posture or security policies and procedures, contact Darren Hulem at the contact info below.