August 12, 2021
GRF Cybersecurity Risk Assessment and Scorecard Blog Series
The threat of cyberattacks is frightening, persistent, and can affect any organization, big or small. One way to mitigate this risk is to be sure your computer software and operating systems are up to date. Software vendors regularly release system updates, or “patches,” which are designed to improve the security of a system and protect against vulnerabilities.
A 2019 study done by ServiceNow and the Ponemon Institute found that 60 percent of data breaches were due to failure to apply patches for known vulnerabilities. In short, the breaches could have been prevented by conducting regular updates.
In fact, the massive data breach at Equifax in 2017 happened because a widely known vulnerability was not patched. Equifax did not have a policy in place to update their systems. Thus, hackers were able to access Equifax’s web portal and other network servers and download large amounts of personal customer information.
Similarly, it’s crucial to review our organization’s IT assets. Old servers that are no longer supported can give attackers an entry point into your network. If your organization still uses older versions of Microsoft or Linux, then you are susceptible to attacks. For example, Microsoft announced in 2020 that it is no longer supporting the Windows 7 operating system with software updates.
Best Practices and Processes for Patch Management
To protect your systems, it is crucial to follow best practices and constantly evaluate your cybersecurity posture.
- Account for all assets that are on your network.
- Read the description of the released patch to understand its importance. Does it improve functionality or patch a critical vulnerability?
- When deploying the patch, first run it on a test system that is identical to your active servers. This will allow you to identify any issues with the update.
- Before deploying the patch to all your systems, identify a small number of systems to deploy it to, then deploy the rest in stages. The rollout of critical security patches should occur more quickly while still testing while functionality updates can roll out at a slower pace.
- Make sure your organization has a backout plan to allow for back out of the patch and return to previous operations in case the patch negatively impacts the network.
- Document patches that you are deploying, the importance of them, and any issues you notice.
- Stay up to date with patch releases. Account for the most common day of software releases.
- Continuously monitor your systems to ensure that vulnerabilities are accounted for.
How GRF Can Help
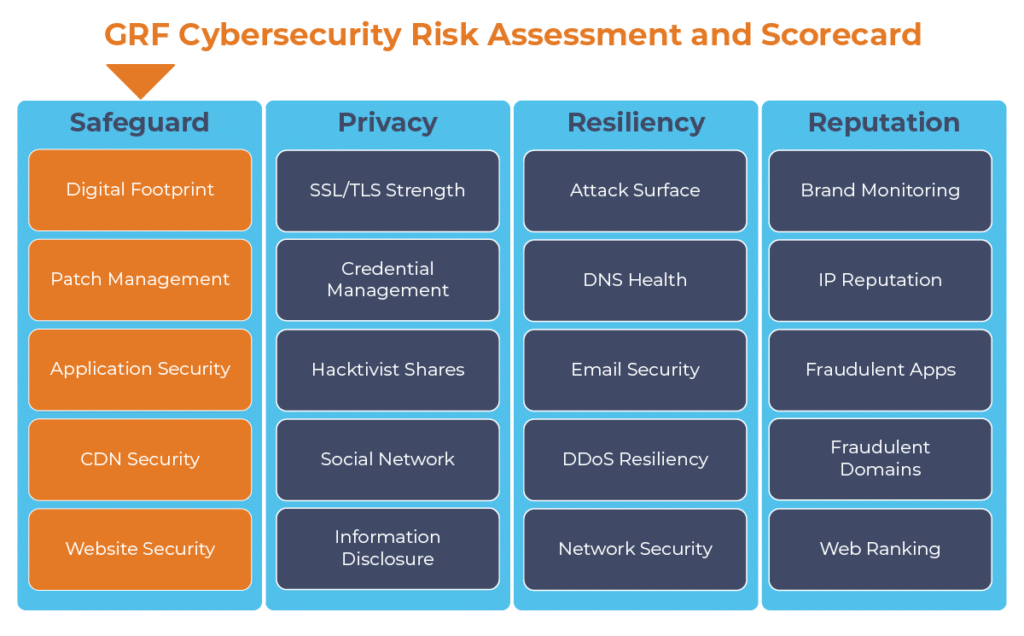
The constant release of patches from software vendors can make it difficult to keep systems up to date. GRF can help you keep track of new patches as they are released and match them to your organization’s system. As part of our cybersecurity audits, GRF offers a Cybersecurity Risk Assessment and Scorecard, a dashboard that continuously monitors internet-facing systems to identify any vulnerabilities.
For more information on GRF’s Cybersecurity Risk Assessment and Scorecard, or about our cybersecurity capabilities, reach out to our IT & Risk Supervisor Darren Hulem, CISA, Security +, or Risk Analyst Tom Brown, CAPM, through our contact us page.
The digital transformation happening in the workplace requires heightened awareness of your organization’s cybersecurity posture. Managing the risks has become another full-time job. The GRF Cybersecurity Risk Assessment and Scorecard helps identify possible weaknesses and vulnerabilities by evaluating risk in 20 different categories. The scorecard will evaluate your cyber posture, propose remediation steps, and help eliminate vulnerabilities that your organization is facing.