October 4, 2021
GRF Cybersecurity Risk Assessment and Scorecard Blog Series
Hackers and malicious attackers will often publicize their targets in various forums or on the dark web, so they can gather support and intelligence for taking down a website or finding vulnerabilities within an organization.
Hacktivists are hackers who are politically and/or socially motivated. Their targets are typically organizations that they disagree with. One of the most well-known hacktivist organizations is Anonymous, which is a decentralized group that performs cyber-attacks on organizations. Their most famous attack was on the Church of Scientology, where the group performed various online attacks to disrupt the church’s operations. They are also known for recently hacking into Epik, an internet service provider used by many far right groups, and publicly posting the private data of the company’s customers.
Anonymous may be the most famous of the hacktivist groups, but other groups may emerge that are not as famous. There are many dark web forums that share information about target companies, and it is important to know when your organization is being talked about, so you can know if your organization is a target.
How do you know if you are targeted?
To find hackers talking about your organization, you will need to search resources that scan the dark web looking specifically at forums, criminal sites, and hacktivist sites. These can be classified by Hacker forums, Whistle Blowing Sites, and other websites related to hackers targeting companies. By narrowing down your organization’s name and web domain(s), you can track whether you are a target of a potential attack as well as seeing if your organization has recently been talked about on underground forums.
Best Practices
- When your organization is identified in underground forums, the best thing to do is review the information that was shared and identify if it is confidential, determine if passwords need to be changed, contacting associated clients, etc.
- Revisit your cyber insurance policy to identify what coverage you have in case of a breach and contact your provider if a breach has occurred.
- If a leak is found from your organization or from a third-party that is associated with you, contact authorities and begin a forensic investigation.
- If you find sensitive content from your organization online, attempt to remove it with the help of the police or the local field office of the FBI.
- If the information is posted on your own website, you can immediately remove it. Online data is also stored, or “cached” by servers and search engines. You may need to contact search engines to ensure that they don’t archive personal information posted in error.
- Search for your company’s exposed data online. If information turns up on other websites, contact the administrator of those sites and ask them to remove it.
How GRF can help
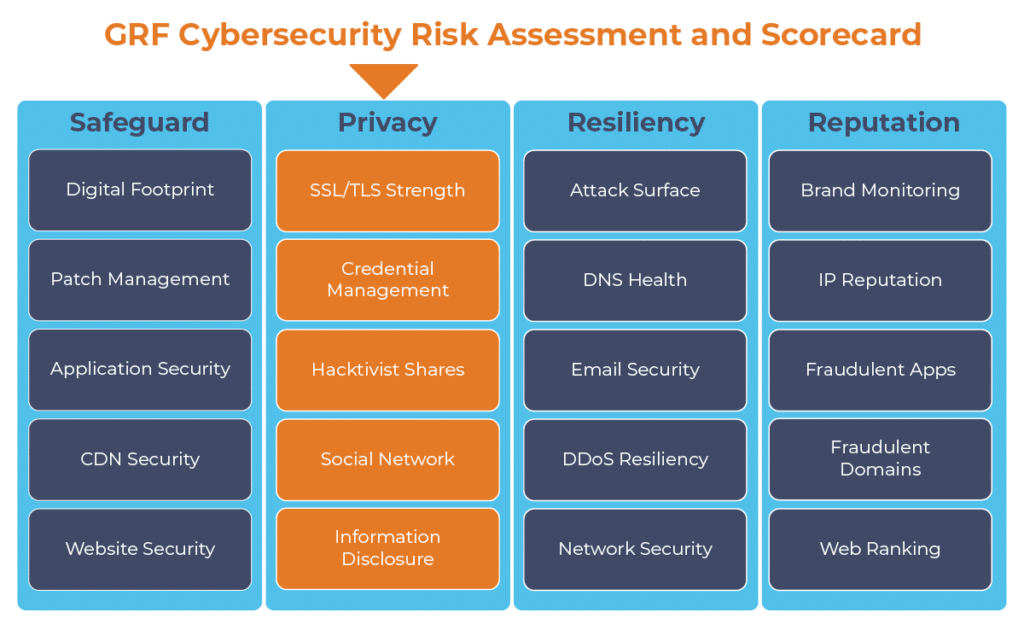
The persistent threat of being a victim of a hacktivist attack creates a need for constant monitoring of underground forums. As part of our cybersecurity audits, we offer our Cybersecurity Risk Assessment and Scorecard, a dashboard that continuously monitors internet-facing systems to identify any vulnerabilities. One component of the scorecard scans and queries your organization’s name and web domains, and provides updates and alerts on your organization’s underground reputation.
For more information on GRF’s Cybersecurity Risk Assessment and Scorecard, or about our cybersecurity capabilities, reach out to our IT & Risk Supervisor Darren Hulem, CISA, Security +, or Risk Analyst Tom Brown, CAPM, through our contact us page.
The digital transformation happening in the workplace requires heightened awareness of your organization’s cybersecurity posture. Managing the risks has become another full-time job. The GRF Cybersecurity Risk Assessment and Scorecard helps identify possible weaknesses and vulnerabilities by evaluating risk in 20 different categories. The scorecard will evaluate your cyber posture, propose remediation steps, and help eliminate vulnerabilities that your organization is facing.